In today’s fast-paced digital landscape, businesses depend on robust IT systems to drive growth, streamline operations, and stay ahead of the competition. But this reliance also exposes them to increasingly complex cyber threats. A comprehensive IT risk assessment—integral to effective IT consulting and advisory services—provides a roadmap for identifying, understanding, and addressing these risks, helping ensure business continuity and protect valuable data.
Whether you’re an enterprise or a startup, leveraging IT advisory services can help you implement the right strategies to proactively manage your IT risks. If you’re looking for customized IT services advisory, reach out to us today to discuss how Straco Advisory Services can support your business with on-demand advisory expertise.
Understanding IT Risk Assessment in 2024
An IT risk assessment, a cornerstone of IT consulting services and advisory consulting, is a structured evaluation of your organization’s exposure to threats. It identifies vulnerabilities—stemming from cyber threats, hardware issues, human error, or even natural disasters—allowing businesses to proactively safeguard essential systems.
Benefits of an IT Risk Assessment:
- Minimizes Downtime: Plans for fast recovery, enabling continuous operations.
- Protects Sensitive Information: Enhances data security and compliance.
- Builds Stakeholder Confidence: Demonstrates proactive cybersecurity.
- Reduces Operational Costs: Avoids costly incidents by addressing vulnerabilities early.
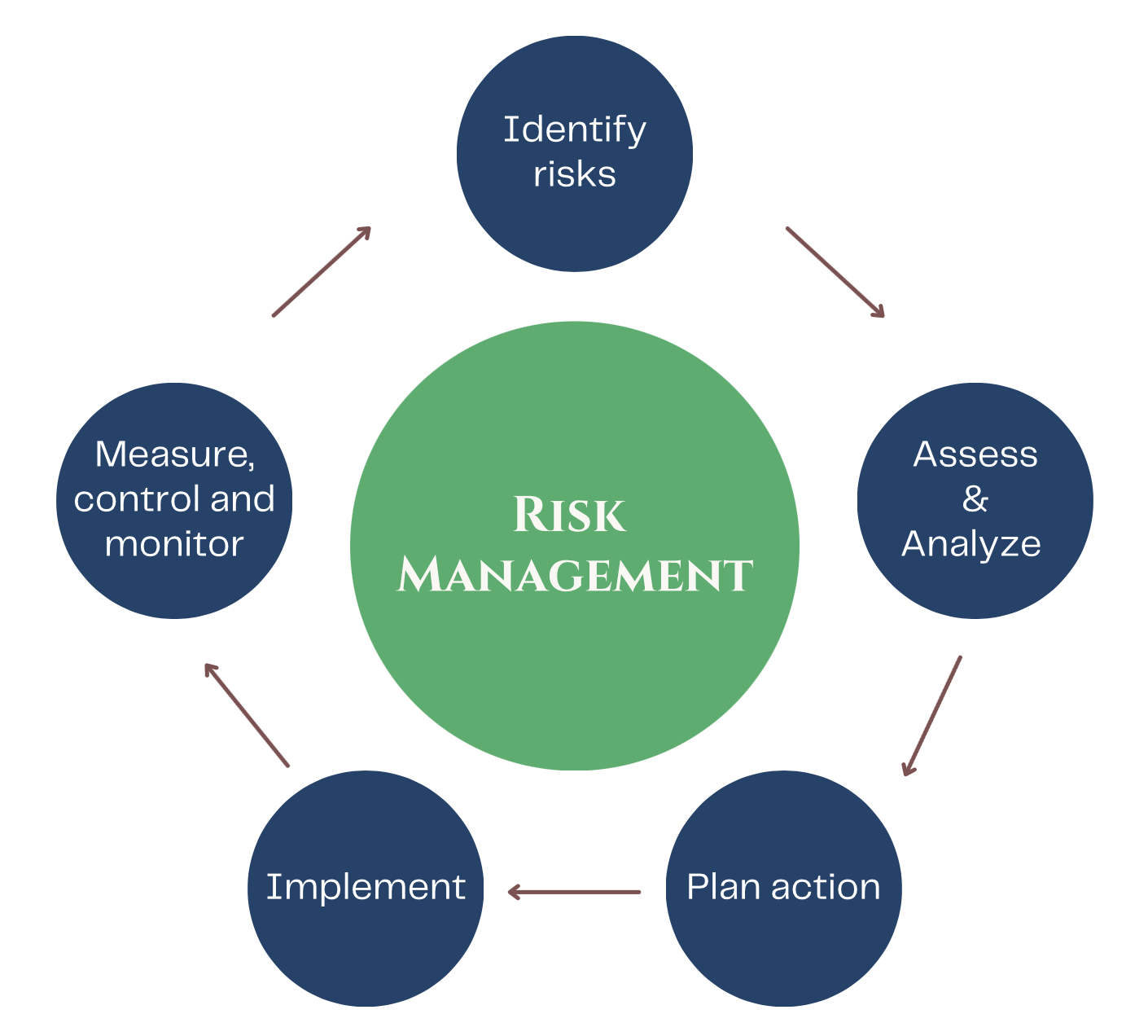
Steps to Conducting an Effective IT Risk Assessment
Engaging in IT risk assessment involves a structured approach, whether internally managed or through IT services advisory.
1. Define the Scope
A clear assessment scope directs focus to high-risk areas:
- Specify systems and data in focus.
- Outline types of risks (cybersecurity, hardware, data loss).
- Define roles involved in the risk assessment.
2. Identify Critical Assets and Data
Recognize and categorize essential assets:
- Hardware: Servers, computers, network devices.
- Software: ERPs, CRMs, proprietary applications.
- Data: Sensitive client data, financial records, and employee information.
3. Recognize Potential Threats
Anticipate a variety of risks:
- Cybersecurity Threats: Ransomware, malware, phishing.
- Physical Threats: Disruptions from natural events or power failures.
- Internal Threats: Unintentional or intentional risks from employees or contractors.
- Technology Failures: Downtime due to outdated systems or malfunctions.
4. Evaluate System Vulnerabilities
Identify system weaknesses that threats can exploit:
- Outdated Software: Higher vulnerability to cyberattacks.
- Weak Access Controls: Lack of secure authentication protocols.
- Insufficient Backup: Inadequate backup strategies heighten data loss risks.
5. Determine Risk Likelihood and Impact
Using a risk matrix, measure:
- Likelihood: Probability of occurrence.
- Impact: Potential damage or disruption.
6. Establish Risk Tolerance
Define your organization’s acceptable risk threshold, with guidance from stakeholders, to balance operational needs with security.
7. Implement Mitigation Strategies
Put targeted controls in place:
- Preventive: Firewalls, antivirus, system updates.
- Detective: Real-time monitoring, intrusion detection systems.
- Corrective: Failover systems, data recovery plans.
8. Document a Risk Management Plan
A well-documented risk management plan provides a clear reference during incidents, listing risks, mitigation measures, and responsible personnel.
9. Regular Monitoring and Review
The IT risk landscape is dynamic, so ongoing assessment is key to staying current with emerging threats and maintaining compliance.
Essential Tools for IT Risk Assessment
Collaborating with IT advisory services or using advanced tools can streamline assessments:
- NIST Cybersecurity Framework: A structured approach to cybersecurity risk.
- ISO/IEC 31000: ISO Standard for Risk Management
- Vulnerability Scanners: Tools like Nessus and Qualys to uncover weaknesses.
- Risk Management Platforms: Various Commercial Offerings to facilitate your journey. Straco Advisory can help you in Product Selection.
Some key trends that will impact the cyber risk landscape in the near future:
Technology is fast evolving and organizations need to keep pace with it in a balanced manner. Here is a list of some trends that we believe are gaining traction in the market and will have an impact in future:
- AI: While on one hand AI is really impacting businesses in a big way and introducing new risks, it can also assist in managing the risks itself by way of Real-time monitoring of threats, powered by machine learning.
- Zero Trust Architecture: Essential as perimeter-based security wanes.
- Automated Compliance Tools: Streamline regulatory adherence.
- Cyber Resilience: Focus on fast recovery post-disruption.
Conclusion: Proactive Steps Toward IT Security
In an age of rising cyber threats, an IT risk assessment is crucial in building a resilient organization. However, Organizations may face hurdles such as limited resources, complex threats, and personnel shortages while doing an IT Risk Assessment. Partnering with Straco Advisory will provide you with scalable solutions to address these challenges and ensure a proactive approach to IT security, data protection, and compliance.
Ready to strengthen your organization’s IT security? Contact Straco Advisory Services today to discuss a tailored IT risk assessment and advisory consulting solution that meets your business needs.